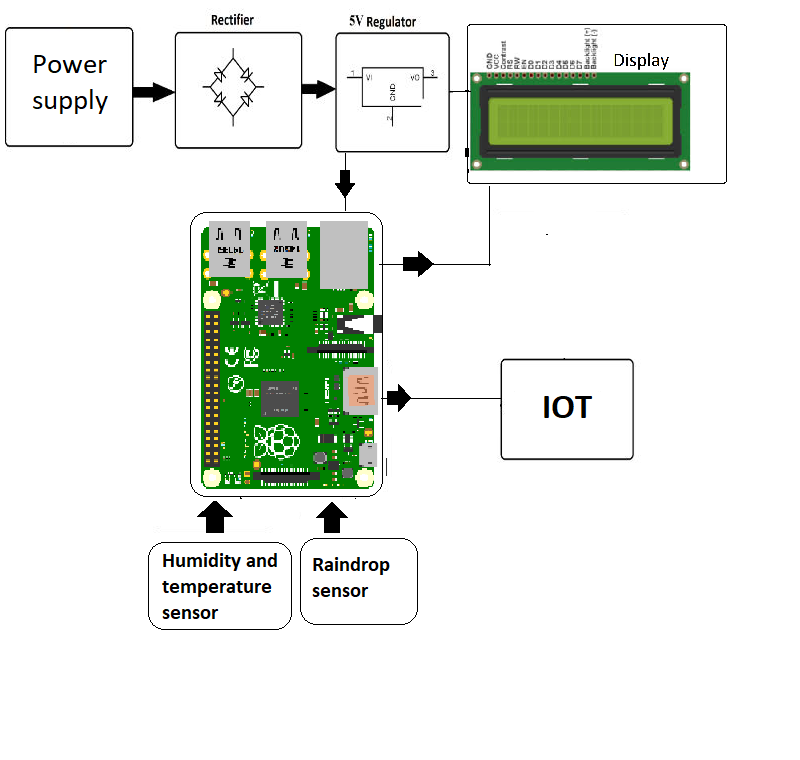
In the ever-evolving landscape of the Internet of Things (IoT) and the increasing need for remote device management, can a small, affordable computer truly stand out as the champion? The answer, emphatically, is yes. The Raspberry Pi, with its unique blend of cost-effectiveness, versatility, and a vibrant community, has become the preferred tool for developers and tech enthusiasts looking to build advanced IoT projects.
The surge in demand for remotely accessible IoT devices is undeniable, fueled by advancements in smart home automation, the rise of industrial monitoring systems, and the expanding field of environmental sensing. But what truly sets the Raspberry Pi apart in this crowded market? Its impressive hardware capabilities, coupled with seamless integration with Secure Shell (SSH), provide a level of flexibility unmatched by many alternatives. Whether you're a seasoned professional or a passionate hobbyist, this compact yet powerful device opens doors to unparalleled possibilities.
Let's delve into the heart of this innovation and understand why the Raspberry Pi reigns supreme as the top SSH remote IoT device. We will explore every facet of its utility, from the initial setup to robust security measures and optimization strategies. This exploration will equip you with the knowledge necessary to confidently harness the Raspberry Pi for your IoT projects, ensuring effortless remote management and a heightened level of functionality.
- Gluck Gluck Origins Cultural Impact Realworld Uses Explained
- Unveiling Lot Lizards A Guide To These Amazing Reptiles
Table of Contents:
- Introduction to Raspberry Pi and SSH
- Raspberry Pi Overview
- Why SSH is Essential for IoT Devices
- Setting Up SSH on Raspberry Pi
- Securing Your SSH Connection
- IoT Applications with Raspberry Pi
- Optimizing Raspberry Pi for Remote Access
- Troubleshooting Common SSH Issues
- Comparison with Other IoT Devices
Exploring Raspberry Pi and SSH
The Raspberry Pi has undeniably become a cornerstone of innovation within the IoT sphere. This compact computer offers an accessible and powerful platform, empowering developers to bring intricate IoT projects to life. Among its many strengths, its exceptional compatibility with Secure Shell (SSH) truly shines. SSH, a protocol designed for secure remote communication, allows users to remotely manage and interact with their Raspberry Pi devices, regardless of their geographical location. Imagine controlling your home's lighting system from across the globe the possibilities are endless.
SSH ensures that all data transmitted between the user and the device remains encrypted and secure, establishing it as the method of choice for remote access. In the context of IoT applications, where devices are frequently deployed in remote and often vulnerable locations, having a reliable and secure connection is paramount. The synergy between the Raspberry Pi and SSH provides a robust solution for managing these devices without compromising critical security protocols. Security is no longer an afterthought; it is the foundation upon which these systems are built.
- Unpacking The Smitty Werbenjagermanjensen Phenomenon Origins Impact
- Squidward Begging Trend Why Its Taking Over The Internet
This section will thoroughly examine the inner workings of SSH and its indispensable role in IoT devices, particularly when partnered with the Raspberry Pi, solidifying its position as a leading technology in this field.
Understanding the Raspberry Pi
The Raspberry Pi's remarkable success stems not only from its capabilities but also from its adaptability. It offers multiple models, each thoughtfully designed to cater to specific use cases and performance demands. The most popular models include:
- Raspberry Pi 4 Model B: With 4GB or 8GB of RAM, this model handles even the most demanding applications with ease, ensuring smooth performance in resource-intensive scenarios.
- Raspberry Pi 3 Model B+: A more budget-friendly option, still delivering commendable performance, making it an excellent choice for general IoT projects where cost-effectiveness is a priority.
- Raspberry Pi Zero W: This compact and lightweight version is the ideal choice for portable IoT devices. Its small size allows it to be seamlessly integrated into projects where space is at a premium.
Each model brings its own strengths to the table, and the ideal choice depends entirely on the specific requirements of your project. For remote IoT applications, models equipped with higher processing power and ample memory are generally the preferred option, guaranteeing optimal performance and responsiveness.
Key Features of the Raspberry Pi
The Raspberry Pi boasts an impressive array of features that make it uniquely suited for IoT projects:
- Compact Design: Its diminutive form factor allows for seamless integration into a variety of environments without demanding much physical space. Its unobtrusive presence makes it a versatile choice for installations in tight quarters or where aesthetics are a key consideration.
- Versatile Connectivity: Equipped with integrated Wi-Fi, Bluetooth, and Ethernet, the Raspberry Pi provides a multitude of connectivity options, allowing it to connect to a wide spectrum of networks and devices. This flexibility simplifies integration into existing infrastructure or the creation of new, interconnected systems.
- Open-Source Community: The extensive and dedicated community of developers that supports the Raspberry Pi ecosystem is unparalleled. This global network contributes a wealth of resources, from tutorials and documentation to pre-built software and troubleshooting guides. The community's collective knowledge is an invaluable asset for any user, from novice to expert.
These features, when combined with its remarkably affordable price point, make the Raspberry Pi the top choice for a multitude of IoT enthusiasts and developers alike.
The Importance of SSH in IoT Devices
Secure Shell (SSH) plays a crucial role in the effective management of IoT devices. It provides a secure channel for remote access, ensuring that all sensitive data and commands are transmitted safely and securely. For IoT devices like the Raspberry Pi, SSH presents several distinct advantages:
- Encryption: All data exchanged through SSH is encrypted. This includes not only sensitive information, but also all commands and responses, safeguarding them against unauthorized interception and mitigating potential security breaches.
- Authentication: SSH supports a variety of authentication methods, including password-based and public key authentication. Public key authentication, in particular, offers an enhanced layer of security, making it significantly harder for malicious actors to gain access to your devices.
- Remote Command Execution: SSH empowers users to execute commands directly on their Raspberry Pi devices remotely. This streamlines management tasks, allows for quick updates, and enables real-time troubleshooting, ultimately simplifying device maintenance and administration.
With the rapidly growing number of cyber threats and the increasing sophistication of malicious actors, securing IoT devices has become more critical than ever before. SSH helps mitigate these risks by providing a robust and secure method for remote access and control, making it an indispensable tool for any serious IoT project.
Configuring SSH on the Raspberry Pi
Enabling SSH
Enabling SSH on the Raspberry Pi is designed to be a straightforward and user-friendly process. To set it up, simply follow these steps:
- First, connect your Raspberry Pi to a monitor and keyboard.
- Open the terminal and type the following command:
sudo raspi-config. This will open the Raspberry Pi configuration tool. - Navigate to "Interfacing Options" and select "SSH".
- Choose "Enable" and then reboot your Raspberry Pi to activate the changes.
Alternatively, if you prefer a more direct approach, you can enable SSH by placing an empty file named "ssh" in the boot partition of your Raspberry Pi's SD card. This method can be particularly useful when you need to configure SSH before the device has even booted up for the first time.
Connecting via SSH
Once SSH is enabled, you are ready to connect to your Raspberry Pi using an SSH client. Popular clients include PuTTY, for Windows, and the built-in terminal applications on both macOS and Linux operating systems. To establish a connection, simply use the following command:
ssh pi@
Remember to replace
Enhancing SSH Security
While SSH itself provides a secure connection, there are several additional measures you can take to significantly enhance its security. Here are some best practices to implement:
- Change Default Credentials: Immediately after enabling SSH, it is crucial to change the default username and password. Select a unique and strong password to mitigate the risk of brute-force attacks.
- Disable Password Authentication: Move towards using public key authentication. It's a more secure and robust method, significantly reducing the vulnerability to password-based attacks.
- Limit Access: Restrict SSH access to specific IP addresses or a defined range of IP addresses using firewall rules. This prevents unauthorized access from unknown sources and further protects your device.
- Use a Non-Standard Port: Change the default SSH port (22) to a less commonly used port. This will help deter automated attacks and reduce the likelihood of your device being targeted by malicious bots.
Implementing these recommended security practices will drastically reduce the risk of unauthorized access to your Raspberry Pi. By diligently following these steps, you can protect your device and maintain the integrity of your IoT projects.
IoT Applications Enabled by the Raspberry Pi
Smart Home Automation
The Raspberry Pi has become a fundamental component in smart home automation projects, revolutionizing how we interact with our living spaces. With SSH, users can remotely control and monitor their smart home devices from anywhere in the world. Think of controlling your lighting, adjusting your thermostat, or monitoring your home security system, all from your phone or computer. Platforms like Home Assistant integrate seamlessly with the Raspberry Pi, providing a centralized hub for managing all your smart home components. It is a powerful, flexible, and cost-effective solution for building your smart home.
Environmental Monitoring
Environmental monitoring is another prevalent application for the Raspberry Pi. Equipped with a range of sensors, the Raspberry Pi can collect and analyze a vast amount of environmental data, including temperature, humidity, air quality, and much more. Through SSH, users can remotely access this valuable data and take immediate action based on the readings, whether it's adjusting ventilation, regulating temperature, or simply tracking trends over time. This makes the Raspberry Pi an ideal tool for scientific research, agricultural applications, or simply monitoring the environment in your own home.
Industrial IoT
In industrial environments, the Raspberry Pi serves as a reliable platform for monitoring and controlling complex machinery. Its ability to handle complex tasks and offer secure remote access makes it an ideal choice for a range of industrial IoT applications. From monitoring production lines to automating maintenance procedures, the Raspberry Pi offers a cost-effective and flexible solution for modernizing industrial operations and enhancing efficiency. The ability to remotely diagnose and repair equipment can save significant time and money by reducing downtime and enabling proactive maintenance practices.
Maximizing Raspberry Pi Performance for Remote Access
To ensure optimal performance for remote access, consider these essential optimization tips:
- Update Software Regularly: Keep your Raspberry Pi's operating system and all installed software up-to-date to receive the latest features, security patches, and performance improvements. Regular updates are critical for both functionality and security, protecting your device from potential vulnerabilities.
- Use a Static IP Address: Assign a static IP address to your Raspberry Pi. This eliminates connection issues caused by dynamic IP changes, which are common on many networks. A static IP ensures reliable remote access, and that you can always find and connect to your device.
- Monitor Resource Usage: Employ tools like `htop` or `glances` to monitor CPU, memory, and disk usage. These tools provide valuable insights into your device's performance, enabling you to identify and address potential bottlenecks. Regularly monitoring resource usage helps ensure optimal performance and identifies any issues that may be hindering remote access.
By following these optimization tips, you can significantly enhance your Raspberry Pi's performance and reliability, ensuring a smooth and dependable experience for all of your remote IoT applications.
Addressing Common SSH Issues
Even with a properly configured setup, you may encounter SSH-related issues from time to time. Here are solutions to some of the most common problems:
- Connection Refused: Ensure that SSH is enabled on your Raspberry Pi and that your firewall configuration allows SSH traffic on the appropriate port. Double-check that no firewall rules are inadvertently blocking the connection.
- Authentication Failure: Carefully verify that the username and password (or public key) you are using are correct. Double-check for any typos or incorrect capitalization. If you're using public key authentication, ensure that the keys have been properly configured.
- Timeout Errors: Check your network connection and verify the Raspberry Pi's IP address. A stable internet connection is essential for SSH. Ensure that there are no network interruptions and that the Raspberry Pi is reachable on your network.
Resolving these issues promptly is critical to maintaining a stable SSH connection for your Raspberry Pi. Troubleshooting these issues promptly and methodically will save you time and frustration.
Raspberry Pi vs. Other IoT Devices
While the Raspberry Pi stands out as a premier choice for IoT projects, other devices such as Arduino, ESP32, and BeagleBone also present compelling solutions. However, the Raspberry Pis strengths give it an edge over its competitors:
- Powerful Hardware: The Raspberry Pi offers superior processing power, memory, and storage capabilities compared to devices like Arduino. This allows it to handle more complex tasks, process larger amounts of data, and run more sophisticated software.
- Rich Software Ecosystem: The Raspberry Pi benefits from a vast and well-established software ecosystem, including a wide array of libraries, tools, and development environments. This ecosystem makes it easier for developers to build and deploy their IoT applications.
- Community Support: The Raspberry Pi boasts an active and supportive community that provides extensive resources, tutorials, and troubleshooting assistance. This strong community network is invaluable for both beginners and experienced developers.
These advantages solidify the Raspberry Pi's position as the top SSH remote IoT device for most applications, offering a versatile, powerful, and well-supported platform for a wide range of projects.