In the rapidly evolving landscape of the Internet of Things (IoT) and the ever-growing need for remote device management, could the Raspberry Pi truly be the ultimate Swiss Army knife for developers and tech enthusiasts? The answer, as we shall see, leans heavily towards a resounding yes. Its blend of affordability, adaptability, and robust community backing has cemented its position as a leading contender for building powerful and versatile IoT projects.
The demand for remote IoT devices has surged dramatically in recent years, fueled by significant advancements in several areas. These include the rise of smart home automation, the need for sophisticated industrial monitoring systems, and the increasing focus on environmental sensing applications. Among the myriad of options available to developers and hobbyists, the Raspberry Pi continues to dominate a significant portion of the market. This is largely due to its potent hardware capabilities and seamless integration with SSH (Secure Shell). Whether you are a seasoned professional developer or an enthusiastic hobbyist, this remarkably compact yet powerful device offers unparalleled flexibility and control.
| Feature | Description |
| Hardware Specifications |
|
| Software Ecosystem |
|
| Community and Support |
|
| Cost and Availability |
|
Source: Raspberry Pi Foundation
The very essence of this article is to unravel the reasons behind the Raspberry Pi's standing as the premier SSH remote IoT device. We will meticulously explore fundamental aspects like setup, security considerations, and optimization strategies. Our aim is to provide you with a comprehensive understanding, equipping you with the knowledge to harness the full potential of the Raspberry Pi in your IoT projects, thereby ensuring seamless remote management and enhanced overall functionality.
Let's now delve into how SSH functions and why it is absolutely crucial for IoT devices, especially when they are paired with the Raspberry Pi.
Introduction to Raspberry Pi and SSH
The Raspberry Pi has become a symbol of innovation in the IoT domain, transforming how developers and hobbyists approach the creation of smart devices. This unassuming, credit-card-sized computer presents an incredibly affordable yet potent platform, empowering developers to create and deploy sophisticated IoT projects. A key feature that truly distinguishes the Raspberry Pi, making it almost indispensable, is its built-in compatibility with SSH (Secure Shell). This is a powerful protocol specifically designed to facilitate secure remote communication, allowing users to securely manage and interact with their Raspberry Pi devices from anywhere in the world.
- Blue Bracelet Movement Hope Amp Support For Mental Health
- Sky Bri Feet Exploring The Trend Artistic Expression
SSH provides the crucial advantage of encrypting all data transmitted between the user and the device. This ensures the confidentiality and integrity of the information exchanged, making it the preferred method for remote access. In the context of IoT applications, where devices are often deployed in physically remote or potentially vulnerable locations, having a reliable and secure connection is absolutely critical. The Raspberry Pi, combined with the capabilities of SSH, offers a robust and practical solution for managing these devices without compromising on security.
In the sections that follow, we will explore the inner workings of SSH and underscore its importance for IoT devices, specifically highlighting its perfect synergy with the Raspberry Pi.
Raspberry Pi Overview
Raspberry Pi Models
The Raspberry Pi ecosystem is renowned for its versatility, offering a range of models, each expertly tailored to suit diverse use cases and varying project requirements. The most popular models include:
- Raspberry Pi 4 Model B: This model is known for offering impressive performance with 4GB or 8GB of RAM, making it ideal for demanding applications that require substantial processing power and memory.
- Raspberry Pi 3 Model B+: This model provides a more cost-effective entry point while still delivering decent performance, making it a solid choice for general IoT projects where resources are a key consideration.
- Raspberry Pi Zero W: The Raspberry Pi Zero W is a marvel of miniaturization, presenting a compact and lightweight version. This makes it exceptionally well-suited for portable IoT devices and projects where space constraints are a major factor.
Each model has its own set of strengths, making the ultimate choice dependent on the specific needs of your project. For remote IoT applications, models that offer higher processing power and increased memory capacity are generally preferred to ensure smooth and efficient remote management.
Key Features of Raspberry Pi
The Raspberry Pi boasts an impressive array of features that collectively contribute to its appeal as an ideal platform for IoT projects:
- Compact Size: The remarkably small form factor of the Raspberry Pi is a significant advantage. It allows for seamless integration into a diverse range of environments without taking up excessive space, making it ideal for projects where size matters.
- Versatile Connectivity: The Raspberry Pi is equipped with a range of connectivity options, including built-in Wi-Fi, Bluetooth, and Ethernet. This makes it capable of connecting to a wide array of networks, which is essential for remote access and data transfer in IoT applications.
- Open-Source Community: A thriving and extensive community of developers contributes to the Raspberry Pi's ecosystem. This vibrant community provides an abundance of resources, including extensive documentation, tutorials, and troubleshooting support, ensuring that users have ample assistance when developing their IoT projects.
These features, coupled with its affordability, solidify the Raspberry Pi's position as a top choice for IoT enthusiasts and professionals alike.
Why SSH is Essential for IoT Devices
Secure Shell (SSH) is absolutely pivotal in the realm of IoT device management. It establishes a secure and encrypted channel for remote access, thereby ensuring that all sensitive data and commands are transmitted safely and securely. For IoT devices like the Raspberry Pi, SSH offers several distinct advantages:
- Encryption: The core principle of SSH is to encrypt all data that is exchanged. This robust encryption mechanism provides critical protection against unauthorized access to your data and commands.
- Authentication: SSH supports multiple authentication methods, including password-based authentication and the more secure public key authentication. This provides flexibility while also enhancing the overall security posture of your devices.
- Remote Command Execution: A key benefit of SSH is its ability to remotely execute commands on your Raspberry Pi devices. This functionality streamlines management tasks, allows for automated actions, and enables real-time control over your devices from a distance.
In the face of increasing cyber threats, securing IoT devices is paramount. SSH plays a crucial role in mitigating these risks, making it an indispensable tool for all IoT projects, big and small.
Setting Up SSH on Raspberry Pi
Enabling SSH
Enabling SSH on your Raspberry Pi is a relatively straightforward process. Here's a simple step-by-step guide to get you started:
- Connect your Raspberry Pi to a monitor and keyboard.
- Open the terminal and type the command:
sudo raspi-config. - Navigate through the menu using the arrow keys and select "Interfacing Options," then proceed to select "SSH."
- Choose the "Enable" option and then reboot your Raspberry Pi to apply the changes.
Alternatively, there's another method for enabling SSH: you can simply place an empty file named "ssh" in the boot partition of your Raspberry Pi's SD card. This will automatically enable SSH on the first boot.
Connecting via SSH
Once you have successfully enabled SSH, the next step is to establish a connection to your Raspberry Pi. You can accomplish this using an SSH client such as PuTTY (for Windows) or through the built-in terminal on macOS and Linux. To establish a connection, use the following command:
ssh pi@
Make sure to replace with the actual IP address of your Raspberry Pi. You can usually find this IP address on your network router or by checking the Raspberry Pi's display if it's connected to a monitor.
Securing Your SSH Connection
While SSH itself offers a secure connection, implementing additional security measures will significantly bolster the protection of your Raspberry Pi. Here are some best practices to consider:
- Change Default Credentials: A critical first step is to update the default username and password. Choose a unique and strong password that's difficult to guess or crack.
- Disable Password Authentication: For an even more secure setup, consider using public key authentication. This method is generally considered more secure than relying solely on passwords.
- Limit Access: Restrict SSH access to specific IP addresses. This adds an additional layer of security by only allowing connections from trusted sources.
- Use a Non-Standard Port: Change the default SSH port (22) to a less common port. This will help deter automated attacks that target the default port.
Implementing these security measures will significantly minimize the risk of unauthorized access to your Raspberry Pi and the data it processes.
IoT Applications with Raspberry Pi
Smart Home Automation
The Raspberry Pi has become a cornerstone of smart home automation projects. With SSH, users gain the ability to remotely control and monitor their smart home devices. These include lights, thermostats, security systems, and a wide range of other connected appliances. Popular platforms like Home Assistant integrate seamlessly with the Raspberry Pi, providing a centralized hub for managing all your smart home components. This allows for comprehensive control and automation from anywhere in the world.
Environmental Monitoring
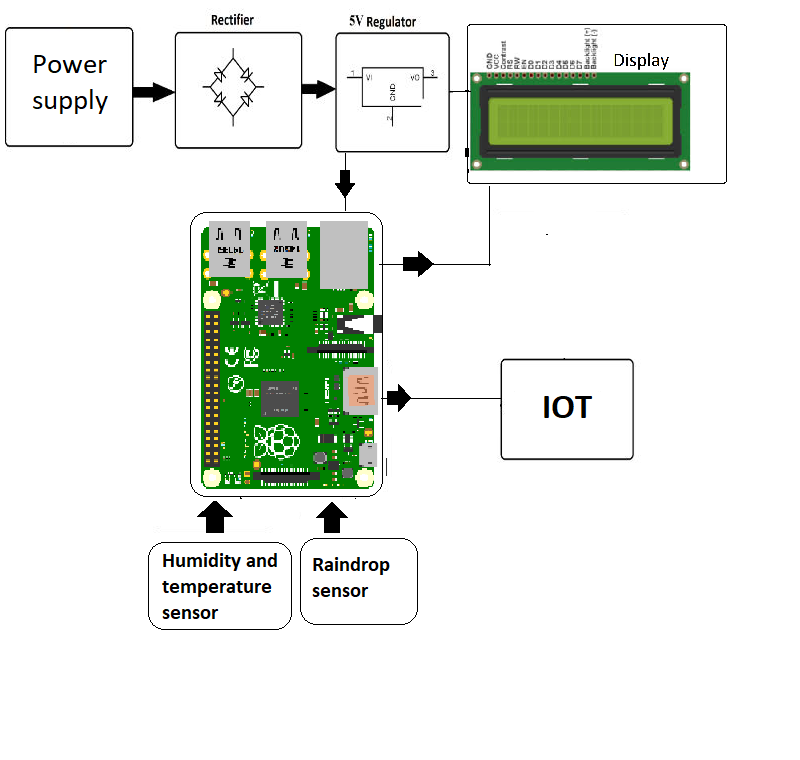
Environmental monitoring is another common application for the Raspberry Pi. Equipped with various sensors, the Raspberry Pi can collect and analyze data on critical environmental factors. This data often includes measurements of temperature, humidity, air quality, and more. Through SSH, users can remotely access this valuable data, enabling them to make informed decisions and take any necessary actions based on the real-time readings.
Industrial IoT
In industrial settings, the Raspberry Pi is deployed as a reliable platform for monitoring and controlling machinery. Its capacity to handle complex tasks, along with its ability to provide secure remote access, makes it an ideal choice for industrial IoT applications. This is particularly useful for tasks such as remote diagnostics, predictive maintenance, and ensuring operational efficiency in industrial environments.
Optimizing Raspberry Pi for Remote Access
To ensure optimal performance for remote access, consider the following tips:
- Update Software Regularly: Keep your Raspberry Pi's operating system and installed software up to date. This ensures you benefit from the latest features, security patches, and performance improvements.
- Use a Static IP Address: Assign a static IP address to your Raspberry Pi. This avoids potential connection issues that can arise when the IP address dynamically changes.
- Monitor Resource Usage: Employ tools such as `htop` or `glances` to monitor the CPU usage, memory consumption, and disk usage. This helps to ensure your Raspberry Pi is not overloaded, which could hinder remote access capabilities.
By optimizing your Raspberry Pi, you can significantly enhance its performance and the overall reliability of remote IoT applications.
Troubleshooting Common SSH Issues
Even with the proper setup, issues related to SSH can arise. Here are some common problems and their respective solutions:
- Connection Refused: If you encounter a "Connection Refused" error, make sure that SSH is enabled on your Raspberry Pi. Furthermore, ensure that the Raspberry Pi's firewall allows SSH traffic to pass through.
- Authentication Failure: If you see an "Authentication Failure" error, carefully verify that the username and password (or your public key, if you are using key-based authentication) are entered correctly. Double-check for any typos.
- Timeout Errors: If you experience "Timeout Errors," it's important to verify your network connection and ensure that the Raspberry Pi's IP address is correct. If problems persist, you might need to investigate your router settings.
Addressing these issues promptly is essential for maintaining a stable SSH connection to your Raspberry Pi.
Comparison with Other IoT Devices
While the Raspberry Pi remains a top contender for IoT projects, other devices like Arduino, ESP32, and BeagleBone also offer compelling solutions. However, the Raspberry Pi distinguishes itself in several key areas:
- Powerful Hardware: The Raspberry Pi offers superior processing power when compared to devices like the Arduino. This allows it to handle more complex tasks and run more demanding applications.
- Rich Software Ecosystem: The Raspberry Pi boasts a vast and extensive software ecosystem. This includes a wide array of libraries and tools that are readily available for developers to use and integrate into their projects.
- Community Support: The Raspberry Pi has a highly active and supportive community. This community provides a wealth of resources, including tutorials, forums, and other support materials that can be invaluable during the development process.
These advantages are significant. They underscore why the Raspberry Pi has emerged as the best SSH remote IoT device for a wide range of applications.
- Unlocking The Magic A Comprehensive Guide To Crystal Fascination
- Blue Bracelet Movement Hope Amp Support For Mental Health